Lotus Training Overview
During this course you will use Domino Administrator as you learn to perform Notes-specific administration tasks such as registering users and controlling Notes configuration using policies.
Lotus Training Learning Objectives
In this course, you will learn how to:
- describe the primary administration concepts of Notes and Domino, including Domino Domain, Organization, Organizational Units, Domino Named Networks, Domino Directory, Registration Server, Home/ Mail Server, Administration Process, and Administration Server
- set up Domino Administrator, configure Administration Preferences, and use Domino Administrator to manage Notes users
- perform a basic Notes user registration to understand the outcomes of the process
- create an Organizational Unit Certifier hierarchy
- configure a Certifier ID to include contact information, ID/Password Recovery Information, multiple passwords, and support for alternate languages and names
- implement the Certificate Authority process, migrate Certifier IDs to the Certificate Authority, and give administrators CAA and/or RA rights
- define explicit and organizational policies with Registration, Setup, Desktop, Archiving, Security, and Mail Settings
- register Notes users using all the options, including ID/Password Recovery Information, the CA Process, and Registration Settings
- define Security Settings to set ECLs, encrypt local replicas, and set Mail security options, and enforce client security settings
- use the Administration Process to automate user identity changes and to recertify expired certificates
- lock out unauthorized users from servers and databases
- enforce passwords and password changes and institute a custom password policy
- recover a lost User ID or forgotten password
- deploy local replica databases, a Mobile Directory Catalog, custom Welcome Pages, Bookmarks, and custom tips of the day
- upgrade Notes software using Upgrade By Mail and Notes Smart Upgrade
- define a policy to control user Mail preferences
- define policy hierarchies that inherit or enforce settings
- track active Notes and other client users to ensure license compliance
Lotus Training Audience
This course is designed for administrators responsible for managing Notes clients.
Whereas the Lotus Domino 7 Administration Basics course covers general Domino Server installation and configuration, this course focuses on the administration of Notes clients.
This course is also distinguished from the Lotus Notes 7 Support course, which is designed for help desk personnel who do not have Domino Administrator or administrative rights to the Domino Server but who are responsible for installing, setting up, and supporting Notes clients. Depending on your responsibilities, you may need the additional knowledge presented in this course to learn the administrator side of supporting Notes clients.
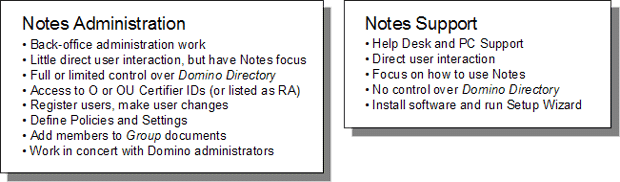
While ideally you will have completed the Domino 7 Administration Basics course before taking this course, doing so is not required. The first Topic in this course reviews the necessary concepts of Notes administration and how to use Domino Administrator.
This course is part of a series of Domino administration training courses. Follow these paths to master all aspects of administering the Domino Server, Lotus Notes, and other clients:
 Courses later in the series assume that you have mastered the content of earlier courses.
Courses later in the series assume that you have mastered the content of earlier courses.
This course is designed for administrators who are responsible for supporting Lotus Notes clients and who:
- may have never administered a Domino Server
- are proficient Lotus Notes 7 users.
You will find this course most useful if prior to this course you have:
- studied the principles and operation of personal computer networking using TCP/IP in LAN/WAN/Internet environments
- installed and supported the operating system used in this course (Windows 2000 Server and Professional), as well as applications used by those systems
- installed, administered, and supported network operating system server and workstation software.
You will find the course especially rewarding if you have already installed a Domino Server and a handful of Notes clients and have had some experience designing Domino databases.
Lotus Training Course duration
This course is sold as a 3-day course.
Lotus Training Course outline
Topic 1: Domino Administrator
Start Domino Administrator
Exercise: Set up Domino Administrator
User interface
Administration Preferences Basics tab
Sequence to use Domino Administrator
Get Administrator Help
Exercise: Domino Administrator interface
Remote Server Console
Administrator use of Domino Administrator
Full Access administrator mode
Administrator access to the Domino Directory
Administrator access to system databases
Group administration duties
Topic 2: Basic Notes User Registration
What is Notes user registration?
The role of a Person document
Incidental results of user registration
No user count limitations
Results of first server setup
Review of administrative rights required to register a user
Exercise: Basic Notes user registration
Topic 3: Organizational Units
Hierarchy of Certifiers
Advantages of Organizational Units
Disadvantages of Organizational Units
Register users with Organization Certifier
Create OU Certifier from Organization Certifier
Create OU Certifier from OU Certifier
Exercise: Create Organizational Unit Certifier
Exercise: Register user under Organizational Unit
Certifier ID file security
Organizational Unit Administrators
Extended ACL
Enable xACL
Define the xACL
Extended Administration Server
Topic 4: Prepare Certifiers
Task 1: Add Contact information to the Certifier document
Task 2: Add ID/password recovery information to the Certifier ID
Exercise: Add recovery information
Task 3: Add multiple passwords to the Certifier ID
Task 4: Add support for alternate languages to a Certifier ID
Topic 5: Certificate Authority Process
Certificate IDs versus CA Process
Advantages of using the CA Process
Prerequisites to configure the CA Process
CA Process configuration
Step 1: Migrate the Organization Certifier ID to the CA Process
Step 2: Unlock or activate the Certifier
Step 3: Migrate any OU Certifier IDs to CA Process
Step 4: Add or delete CAAs or RAs
Step 5: Register users with CA Process
Exercise: Migrate OU Certifier to CA Process
Topic 6: Prepare Policies and Settings
Policy defined
Settings documents
Policy type
Choosing between Explicit and Organizational policy types
Exercise: Create Policy and Settings documents
Assign policies to users
Assignment Method 1: Set default policy for registrations
Assignment Method 2: Assign policy during registration
Assignment Method 3: Change Person document
What you cannot control with policies
Lock down settings
Topic 7: Prepare to Register Users
Task 1: Ensure that new users have unique names
Task 2: Add user to appropriate group(s)
Task 3: Define Registration Settings policy
Exercise: Registration Settings
Task 4: Set Administration Preferences
Exercise: Set Administration Preferences
Task 5: Define Setup Settings policies
Exercise: Setup Settings
Topic 8: Notes User Registration
Register tool
Basics tab
Mail tab
Address tab
ID Info tab
Groups tab
Roaming tab
Other tab
Exercise: Register user
Registration Queue
Other sources for user names and settings
Register users from a text file
Import text file contents
Windows directory integration
Exercise: Set up Notes user
Topic 9: Security Policies
Execution Control Lists and Design signatures
Administrator control over ECLs
Administration ECL
Refresh client ECL with Administration ECL
Admin ECL in the Security Settings policy document
Exercise: Security Settings policy
Encrypt replica databases on laptops
Replica encryption in the Desktop Settings policy document
Notes mail security
Force encryption of all incoming mail at the server
Mail Security in the Desktop Settings policy document
Exercise: Desktop Settings policy
Security settings in User Preferences
Security settings in Location document
Topic 10: User ID Changes
Administrator access requirements
Procedure 1: Rename user (Administrator initiated)
Exercise: Rename user
Revert user rename change if timed out or rejected
Rename Web-only users
Find Users
Procedure 2: Rename user (User initiated via Notes Mail)
Procedure 3: Move user to another Organizational Unit
Procedure 4: Recertify expiring User ID (Administrator initiated)
Exercise: Recertify User ID
Procedure 5: Recertify expiring User ID (User initiated)
Procedure 6: Recertify expired User ID
Procedure 7: Update users Private and Public Keys
Procedure 8: Delete user
Procedure 9: Lock out user from servers
Procedure 10: Rename or delete group
Procedure 11: Re-register user
Procedure 12: Set recovery information after registration
Topic 11: Password Control
User ID responsibilities
Default password behavior
Password strength
Custom password policy
Increase password security with password verification
Enable password verification and set expiration
How password verification and expiration work
Password verification and expiration anomalies
Lock out User ID
Compare Public Keys
Minimum and maximum client level
Internet password synchronization with Notes ID password
User override of Internet password synchronization
Windows Server password synchronization
Topic 12: User ID and Password Recovery
Problem 1: Lost User ID
Problem 2: User ID file is deleted by the user
Exercise: Recover ID file
Problems with password recovery
Problem 3: User forgets ID password
Problem 4: User ID password is compromised
Topic 13: Desktop Policies
Deploy replica databases
Deploy Mobile Directory Catalog
Deploy Bookmarks
Deploy custom Welcome Pages
Working in Advanced Mode to create new Welcome Pages
Deploy My Work as Welcome Page
Deploy custom tips of the day
Notes System Diagnostic
Automatic Diagnostic Collection
Configure Automatic Diagnostic Collection
Location document and NOTES.INI variables
Topic 14: Notes Software Update
Notes software installation
Notes upgrade installation
Determine existing version
Upgrade by (Notes) Mail
Notes Smart Upgrade from 6.x to 6.x forward
Smart Upgrade Governor
SUCACHE Server Console commands
Smart Upgrade failover
Smart Upgrade Tracking reports
Smart Upgrade debugging
Seamless Mail Upgrade
Upgrade Mail templates using CONVERT
Upgrade ODS using COMPACT
Topic 15: Mail Policies
Mail Settings document
Differences from other types of policies
Tell AdminP to process Mail Settings
Topic 16: Policy Hierarchies and Inheritance
Policy hierarchies
Create policy hierarchy
Inherit settings assignment
Policy Viewer
Inherit and enforce specific settings in a policy hierarchy
Policy Synopsis tool
Exception policies
Topic 17: Notes License Compliance
Certification Log
Client Access Licenses (CALs)
Server\Licenses view
License tracking
Notes version tracking
|